
Key Takeaways
- Cryptography is the foundational layer of blockchain security, enabling trustless coordination between participants through mathematical guarantees of confidentiality, integrity, and authenticity.
- Public-key cryptography secures user identities and transaction authorization, allowing anyone to verify transactions without revealing private information or relying on centralized intermediaries.
- Hash functions and Merkle trees preserve the immutability and auditability of blockchain data, making it tamper-evident and resilient to malicious modification across distributed nodes.
- Advanced cryptographic innovations, including zero-knowledge proofs and ring signatures, are expanding blockchain’s capacity to deliver private, scalable, and user-friendly applications.
- As quantum computing threatens traditional cryptographic algorithms, the development of post-quantum cryptography is essential for the long-term sustainability and security of blockchain ecosystems.
Cryptography serves as the foundational pillar of blockchain technology, enabling secure, transparent, and decentralized systems. In the realm of cryptocurrencies, cryptographic techniques ensure the integrity, authenticity, and confidentiality of transactions, eliminating the need for centralized authorities. This Innovation and Tech article delves into the intricate relationship between cryptography and blockchain, exploring how mathematical principles underpin the security and functionality of decentralized networks.
The Role of Cryptography In Blockchain
At its core, cryptography is the science of securing information through mathematical algorithms. In blockchain networks, cryptography facilitates secure communication between nodes, ensures data integrity, and authenticates transactions. It allows participants to interact in a trustless environment, where the system’s design guarantees security without relying on intermediaries.
One of the primary applications of cryptography in blockchain is in securing transactions. Each transaction is digitally signed using a private key, creating a unique signature that can be verified by others using the corresponding public key. This mechanism ensures that only the rightful owner can authorize transactions from their account, preventing unauthorized access and double-spending.
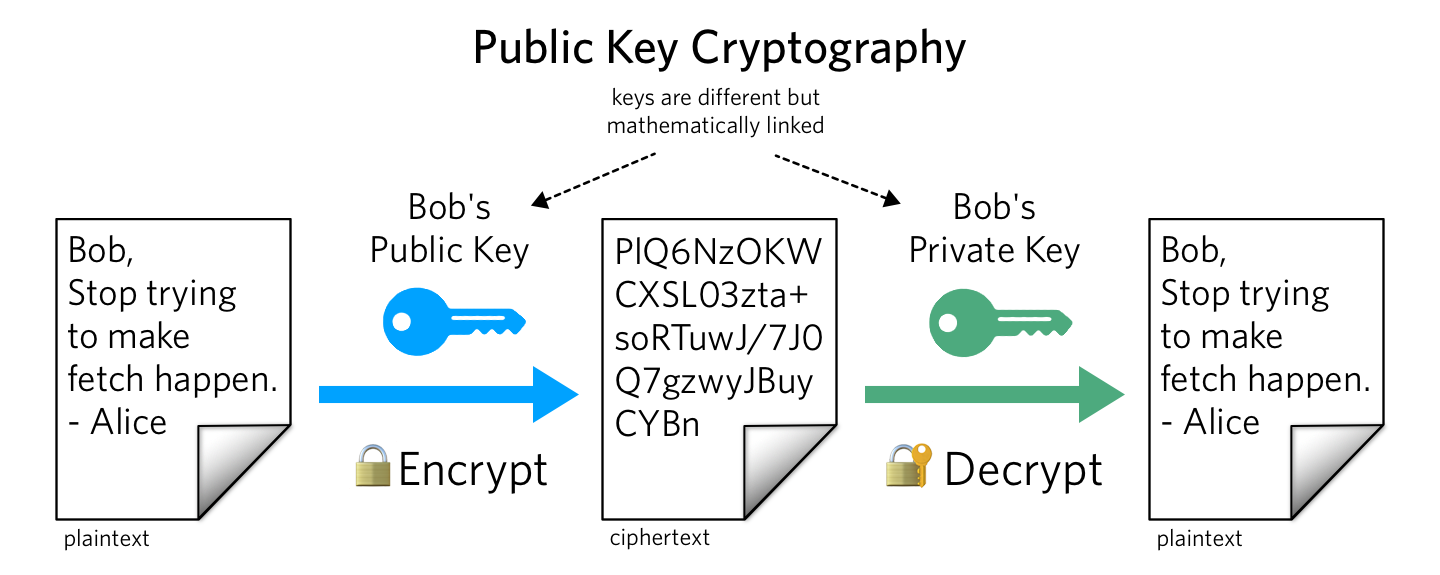
Asymmetric Cryptography: Public & Private Keys
Blockchain systems predominantly employ asymmetric cryptography, also known as public-key cryptography. This method utilizes a pair of keys: a public key, which is openly shared, and a private key, which is kept secret by the owner. When a user initiates a transaction, they sign it with their private key. Network participants can then verify the authenticity of the transaction using the sender’s public key, ensuring that the transaction has not been tampered with and originates from the claimed sender.
This cryptographic approach not only secures transactions but also enables the creation of digital identities. Users can interact pseudonymously on the blockchain, maintaining privacy while ensuring accountability. The public key serves as an address on the network, while the private key grants control over the associated assets.

Hash Functions: Ensuring Data Integrity
Cryptographic hash functions are integral to blockchain’s structure and security. A hash function takes an input and produces a fixed-size string of characters, which appears random. In blockchain, each block contains the hash of the previous block, creating a chain that is resistant to tampering. If any data within a block is altered, its hash changes, breaking the chain and alerting the network to potential fraud.
Moreover, hash functions facilitate efficient data verification through structures like Merkle trees. These trees allow for quick and secure verification of large data sets, enabling lightweight clients to confirm transactions without downloading the entire blockchain.
Digital Signatures: Authenticating Transactions
Digital signatures in blockchain leverage asymmetric cryptography to authenticate transactions. When a user signs a transaction with their private key, it generates a signature that is unique to both the transaction and the key. Other network participants can use the sender’s public key to verify this signature, confirming the transaction’s legitimacy.
This process ensures non-repudiation, meaning the sender cannot deny initiating the transaction, and integrity, as any alteration to the transaction data would invalidate the signature. Digital signatures thus provide a robust mechanism for securing transactions in a decentralized environment.
Advanced Cryptographic Techniques: Enhancing Privacy & Scalability
Beyond basic cryptographic primitives, blockchain systems are increasingly adopting advanced techniques to address privacy and scalability challenges. Zero-knowledge proofs, for instance, allow one party to prove to another that a statement is true without revealing any additional information. This method enhances privacy by enabling transaction validation without exposing transaction details.
Ring signatures and stealth addresses, employed by privacy-focused cryptocurrencies like Monero, obscure the sender and recipient’s identities, making transactions untraceable. These techniques ensure confidentiality while maintaining the network’s integrity.
Scalability solutions also leverage cryptography. Layer 2 protocols, such as payment channels and rollups, use cryptographic proofs to settle transactions off-chain, reducing the load on the main blockchain and increasing throughput.
Post-Quantum Cryptography: Preparing For Future Threats
The advent of quantum computing poses a potential threat to current cryptographic algorithms, particularly those based on factoring large numbers or discrete logarithms. Quantum computers could, in theory, break these algorithms, compromising the security of blockchain systems.
To mitigate this risk, researchers are developing post-quantum cryptographic algorithms that are resistant to quantum attacks. These include lattice-based, hash-based, and multivariate polynomial cryptography. Integrating these algorithms into blockchain protocols is essential to future-proofing the technology against emerging computational capabilities.
Cryptography As The Engine of Decentralized Security
Blockchain’s promise of open, permissionless systems would not be possible without the cryptographic machinery that secures every transaction, block, and identity on-chain. Cryptography does more than protect data, it structures the very logic that enables decentralized consensus, eliminates intermediaries, and transforms trust into a verifiable system property. As blockchain technology evolves, so too must the cryptographic tools that underpin it. From privacy-preserving protocols to quantum-resistant algorithms, the future of Web3 will be written not only in code, but in cryptographic proofs. Understanding and advancing this mathematical foundation is critical to scaling blockchain from niche innovation to global infrastructure.






