Key Takeaways
- Cryptocurrency wallets manage private keys, enabling secure storage and transactions of digital assets on blockchain networks.
- Non-custodial wallets offer complete user control, while custodial wallets rely on third-party services, balancing convenience and risk.
- Hot wallets provide easy access for frequent transactions, whereas cold wallets, like hardware devices, prioritize security through offline storage.
- Hardware wallets, such as Ledger, use secure elements to protect private keys, supporting multiple cryptocurrencies and robust backup options.
- Browser-based and mobile wallets, like MetaMask and FeatherWallet, enhance accessibility, supporting seamless integration with decentralized applications.
Cryptocurrency wallets represent the fundamental infrastructure enabling users to securely manage, store, and transact with digital assets in the rapidly evolving blockchain ecosystem. These sophisticated software applications and hardware devices serve as the critical interface between users and blockchain networks, managing the cryptographic private keys that grant access to cryptocurrency holdings.
The significance of cryptocurrency wallets extends far beyond simple storage, encompassing complex security mechanisms, user experience considerations, and the delicate balance between accessibility and protection that defines modern digital finance. As blockchain technology matures, cryptocurrency wallets continue to evolve, incorporating advanced features to support diverse blockchain protocols and user needs, ensuring they remain pivotal to the adoption and functionality of digital assets.
This Innovation and Tech article explores how cryptocurrency wallets serve as the gateway to digital asset ownership, combining cryptographic security with user-focused design to power the next phase of blockchain adoption.
Understanding Cryptocurrency Wallets: Architecture & Functionality
Cryptocurrency wallets are sophisticated applications that manage private keys rather than storing actual cryptocurrencies, which exist as data entries on distributed blockchain networks. The wallet’s primary responsibility involves securely maintaining the cryptographic keys necessary to sign transactions and prove ownership of digital assets. Modern wallet implementations make blockchain technology accessible to mainstream users by abstracting the complex manual processes that characterized early cryptocurrency transactions, when users needed to manually enter lengthy cryptographic keys for each operation.
Today, wallets provide intuitive interfaces that streamline transaction processes, support multi-chain compatibility, and integrate with decentralized finance (DeFi) platforms, enabling users to engage with a wide range of blockchain-based services.
The fundamental architecture of cryptocurrency wallets centers on the relationship between public and private keys, where the private key serves as the ultimate proof of ownership and control over associated digital assets. When users initiate transactions, wallets utilize these private keys to create cryptographic signatures that validate the transaction’s authenticity without revealing the private key itself. This process ensures that only the legitimate owner can authorize asset transfers while maintaining the security and integrity of the underlying blockchain network.
Additionally, modern wallets often incorporate advanced features such as multi-signature authentication, which requires multiple private keys to authorize a transaction, enhancing security for high-value transfers or shared accounts.
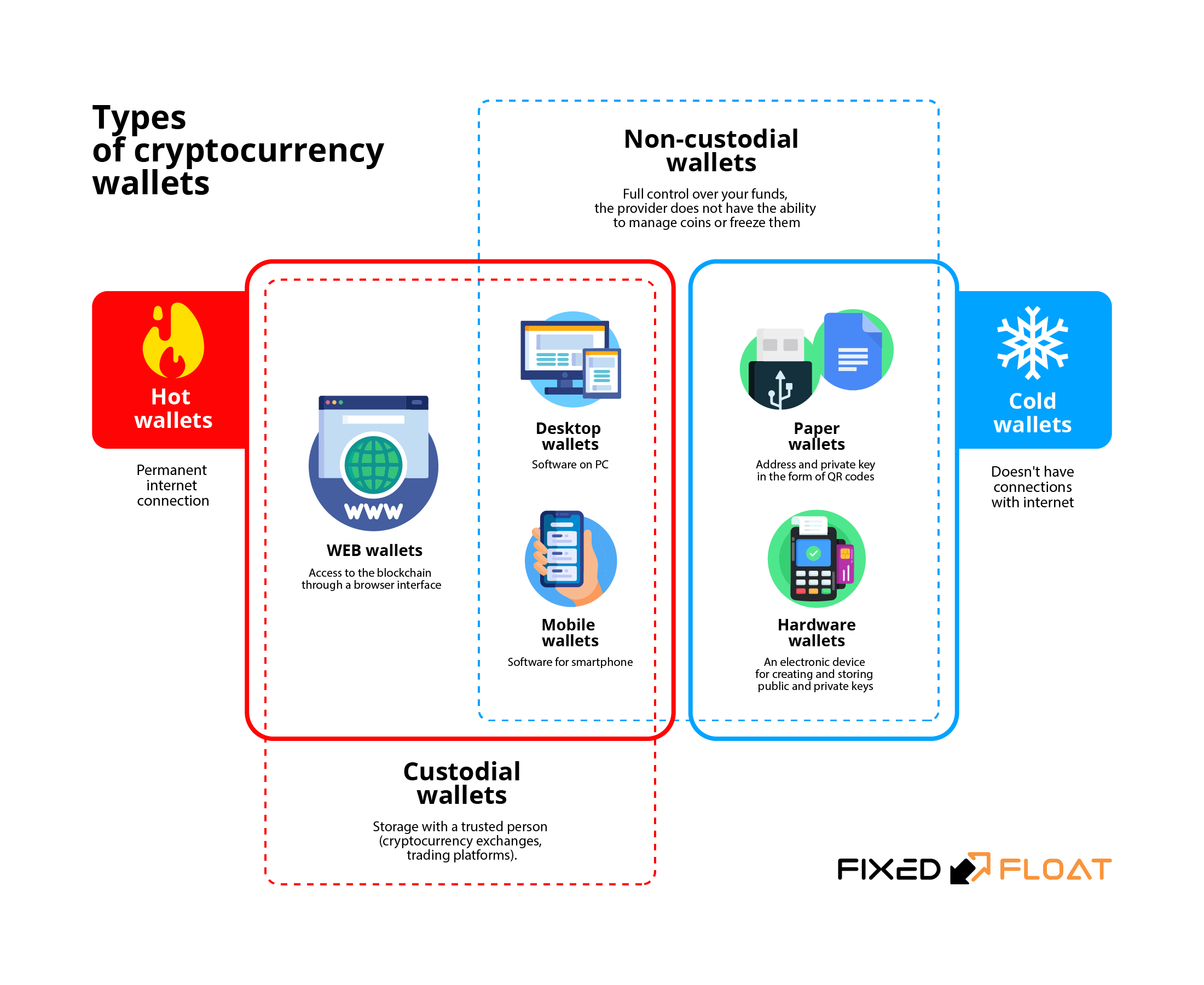
Cryptocurrency Wallets: Custodial vs Non-Custodial Solutions
The cryptocurrency wallet ecosystem divides into two primary categories based on key management responsibility: custodial and non-custodial solutions. Non-custodial wallets grant users complete control over their private keys, making them solely responsible for managing and securing their digital assets. These solutions ensure that funds remain under exclusive end-user control, eliminating reliance on third-party intermediaries such as exchanges or financial institutions.
The autonomous nature of non-custodial wallets aligns with cryptocurrency’s foundational principles of decentralization and self-sovereignty. Moreover, non-custodial wallets often support advanced features like direct integration with decentralized exchanges and staking protocols, allowing users to participate in blockchain governance and earn rewards without relinquishing control.
Custodial wallets, conversely, delegate key management responsibilities to third-party service providers, typically cryptocurrency exchanges or specialized wallet services. While custodial solutions reduce the technical burden on users and provide familiar interfaces reminiscent of traditional banking, they introduce counterparty risk and require users to trust external entities with their valuable digital assets.
These wallets often offer additional services, such as integrated trading platforms, fiat on-ramps, and customer support, making them appealing to novice users. The choice between custodial and non-custodial solutions often reflects users’ technical expertise, security preferences, and comfort level with personal responsibility for asset protection, with many users opting for a hybrid approach to balance convenience and control.
Hot & Cold Wallet Classifications
The wallet landscape further differentiates between hot and cold storage solutions based on internet connectivity and associated security implications.
Hot wallets maintain constant or frequent internet connections, enabling immediate transaction capabilities and seamless integration with decentralized applications and exchanges. These solutions prioritize user convenience and accessibility, making them ideal for frequent traders and users requiring rapid transaction execution. Hot wallets have evolved to support a wide array of blockchain ecosystems, offering features like real-time portfolio tracking, cross-chain swaps, and integration with DeFi protocols, which enhance their utility for active participants in the cryptocurrency market.
Cold wallets operate offline or with minimal internet connectivity, significantly reducing exposure to online threats. Hardware wallets exemplify cold storage solutions, utilizing physical devices resembling USB drives to store private keys in isolated, offline environments. These devices only connect to internet-enabled computers when users need to sign transactions, maintaining key security through physical isolation from potentially compromised online systems. Cold wallets are increasingly designed to support emerging blockchain technologies, such as Layer-2 scaling solutions and non-fungible token (NFT) management, ensuring they remain relevant for users with diverse digital asset portfolios.
Hardware Wallet Technology & Security
Hardware wallets represent the premium security standard for cryptocurrency storage, utilizing specialized physical devices designed exclusively for private key management and transaction signing. Companies like Ledger offer multiple hardware wallet variants, including the Ledger Flex, Nano S Plus, Nano X, and Stax, each providing multi-currency support and offline key storage capabilities. These devices employ secure elements and dedicated chips designed to resist physical tampering and sophisticated attack methods.
Recent advancements in hardware wallet technology include support for wireless connectivity via Bluetooth, enabling secure interactions with mobile devices, and compatibility with emerging blockchain standards, such as those for tokenized assets and smart contract interactions.
The operational model of hardware wallets involves generating and storing private keys within the device’s secure environment, never exposing these critical credentials to connected computers or networks. When users initiate transactions, the hardware wallet receives unsigned transaction data through a crypto bridge software interface, signs the transaction internally using stored private keys, and returns the signed transaction for blockchain broadcast.
This process ensures that private keys never leave the hardware device, maintaining security even when connected to potentially compromised computers. Hardware wallets also incorporate user-friendly interfaces and companion applications, which simplify asset management and provide real-time insights into portfolio performance.
Hardware wallets support multiple cryptocurrencies simultaneously, allowing users to manage diverse digital asset portfolios from a single device. Most hardware wallets implement backup and recovery mechanisms using seed phrases or PIN codes, enabling users to restore access to their funds if the physical device becomes lost or damaged.
The combination of offline storage, specialized security hardware, and comprehensive backup options makes hardware wallets the preferred choice for users with substantial cryptocurrency holdings. Additionally, hardware wallets are increasingly integrating with decentralized identity systems, enabling secure authentication for blockchain-based services without compromising user privacy.
Software & Browser-Based Wallet Solutions
Software wallets encompass a broad category of applications running on computers, smartphones, and web browsers, offering varied functionality and security models. Browser-based wallets like MetaMask have gained significant popularity, particularly for Ethereum ecosystem interactions and decentralized application access.
MetaMask, developed by Consensys, allows users to manage Ethereum-based assets through browser extensions and mobile applications, serving as an intermediary between users and decentralized applications. Recent updates to MetaMask include support for cross-chain bridging, enabling users to transfer assets between different blockchain networks, and enhanced privacy features to protect user data during transactions.
The evolution of browser-based wallets reflects the growing demand for seamless blockchain integration within web environments. These solutions enable websites and decentralized applications to request user authentication, transaction signatures, and smart contract interactions through standardized JavaScript interfaces.
MetaMask exemplifies this trend, incorporating integrated token exchange services and supporting connections to multiple decentralized exchanges to optimize trading rates for users. Furthermore, browser-based wallets are incorporating advanced features like gas fee optimization and support for layer-2 networks, which reduce transaction costs and improve scalability for users engaging with DeFi and NFT platforms.
Mobile wallet solutions address the growing need for portable cryptocurrency access while balancing security and convenience. Recent innovations like FeatherWallet demonstrate efforts to eliminate trust dependencies on centralized servers while maintaining efficient performance on resource-constrained mobile devices. These solutions employ advanced cryptographic techniques, including zero-knowledge proofs, to enable secure wallet synchronization without compromising user privacy or security. Mobile wallets are also expanding to include features like in-app NFT galleries, staking interfaces, and integration with decentralized social platforms, catering to the diverse needs of modern cryptocurrency users.
Shaping The Future Of Digital Asset Storage & Cryptocurrency Wallets
Cryptocurrency wallets have evolved from rudimentary command-line tools into sophisticated applications serving millions of users across diverse blockchain networks. The wallet ecosystem encompasses multiple approaches to balancing security, usability, and functionality, from hardware devices offering maximum security through offline storage to browser-based solutions enabling seamless decentralized application interactions. As the cryptocurrency landscape continues expanding, wallet technologies must accommodate mainstream adoption requirements while supporting the growing complexity of blockchain ecosystems, including DeFi, NFTs, and tokenized assets.
The future of cryptocurrency wallets will likely involve continued innovation in user experience design, enhanced security mechanisms, and improved interoperability across blockchain networks. The ongoing development of embedded wallets, zero-knowledge proof implementations, and cross-chain compatibility demonstrates the industry’s commitment to addressing current limitations while preparing for broader cryptocurrency adoption. Success in this evolving landscape requires balancing the competing demands of security, accessibility, and functionality while maintaining the decentralized principles that define cryptocurrency’s foundational value proposition.