
Key Takeaways
- Darklake’s Innovative Approach: Darklake uses zero-knowledge automated market makers (zkAMMs) to encrypt trade data, preventing MEV-driven frontrunning and sandwich attacks on Solana.
- MEV Mitigation: By integrating zero-knowledge proofs and multi-party computation, Darklake ensures pre- and post-trade privacy, reducing validators’ ability to manipulate transactions.
- DAG-Based Consensus: Darklake adopts a directed acyclic graph (DAG) structure to distribute encrypted transaction shares, enhancing fairness and resisting validator collusion.
- Real-World Impact: Case studies, like the DeezNode incident, demonstrate Darklake’s potential to protect traders from significant financial losses due to MEV exploitation.
- Challenges Ahead: Despite its technical strengths, Darklake faces adoption hurdles due to liquidity fragmentation and regulatory scrutiny, requiring strategic ecosystem partnerships.
The decentralized finance (DeFi) ecosystem on Solana has faced significant challenges due to Maximal Extractable Value (MEV) exploitation, where malicious actors manipulate transaction ordering to extract profits at users’ expense. Darklake, a privacy-focused decentralized exchange (DEX) protocol, has emerged as a critical solution to this problem by integrating zero-knowledge proofs (ZKPs) and multi-party computation (MPC) to protect pre-trade data and mitigate MEV-driven frontrunning. This report analyzes Darklake’s technological framework, its role in addressing MEV vulnerabilities, and its implications for the broader blockchain ecosystem.
By examining real-world case studies of MEV exploitation on Solana and comparing Darklake’s approach to other MEV-resistant protocols, this Crypto Deep Dives article highlights the urgent need for privacy-preserving infrastructure in decentralized trading environments.
Introduction to MEV & Its Impact On Blockchain Ecosystems
The Mechanics Of MEV Exploitation
Maximal Extractable Value (MEV) refers to profits that validators, miners, or automated bots can extract by reordering, inserting, or censoring transactions within a blockchain’s mempool. On Solana, MEV manifests primarily through sandwich attacks, where attackers place two transactions around a victim’s trade to manipulate asset prices. For example, a bot might front-run a large buy order by purchasing the asset first, artificially inflating its price, and then selling it back to the victim at a higher price. This predatory behavior not only erodes user trust but also increases network congestion and transaction costs.
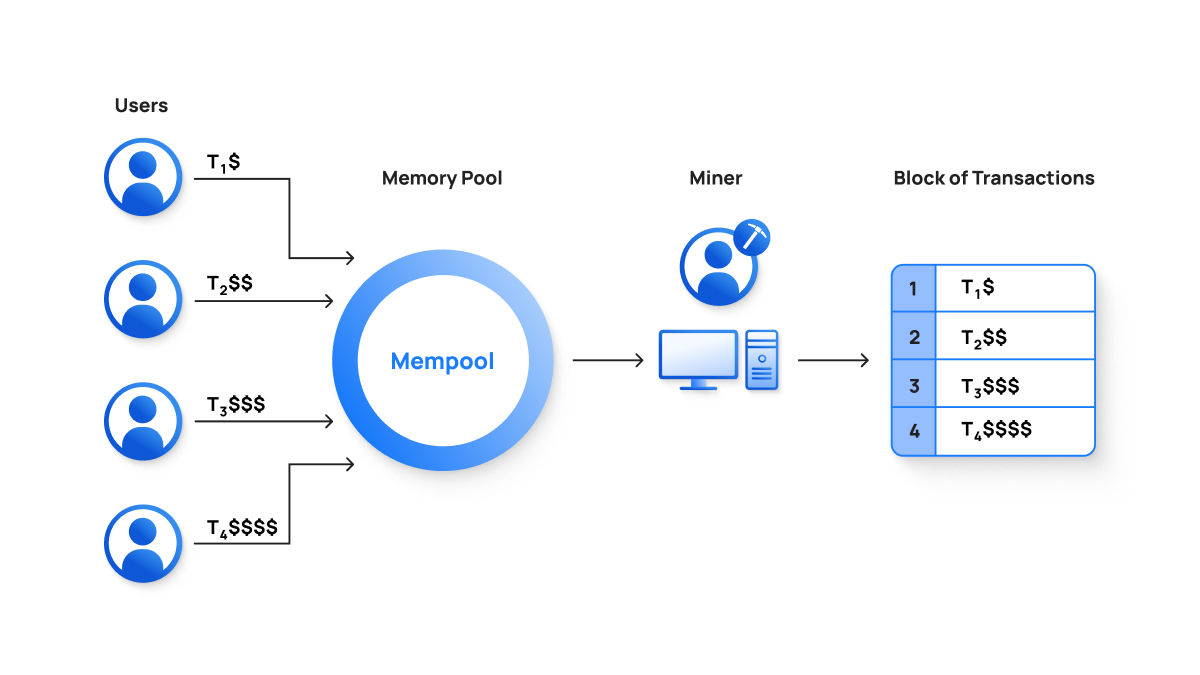
The financial impact of MEV is staggering: in December 2024 alone, the Solana validator DeezNode extracted 65,880 SOL ($13.43 million) through 1.55 million sandwich attacks. Annualized, this would amount to over $163 million in losses for traders. Such exploitation is facilitated by Solana’s high-speed architecture, where validators with privileged access to transaction data can exploit latency advantages.
MEV’s Systemic Risks To Blockchain Networks
Beyond individual losses, MEV poses systemic risks to blockchain consensus stability. When multiple validators compete to exploit the same arbitrage opportunity, they may inadvertently create chain reorganizations or forks, destabilizing the network. Additionally, MEV-driven spam transactions exacerbate congestion, as seen in Solana’s 99% decline in transfer volume from $2 billion to $26 million between November 2024 and February 2025. This collapse in network activity underscores the existential threat MEV poses to decentralized platforms reliant on user participation.
Darklake’s Technological Framework & MEV Mitigation Strategies
Zero-Knowledge Automated Market Makers (zkAMMs)
Darklake’s core innovation lies in its zkAMM protocol, which encrypts critical trade parameters—such as slippage tolerance, order size, and price limits—using zero-knowledge proofs. By obfuscating this data until transactions are finalized, Darklake prevents validators and MEV bots from frontrunning users. For example, a trader’s intent to purchase 100 SOL at a maximum price of $150 remains hidden until the trade is executed, eliminating opportunities for predatory sandwich attacks.
The protocol leverages a hybrid encryption model:
- Pre-trade privacy: ZKPs validate transaction integrity without revealing sensitive details.
- Post-trade privacy: MPC protocols ensure that even after execution, transaction data remains compartmentalized across multiple nodes.
This dual-layer approach addresses both the visibility and timing vulnerabilities that enable MEV exploitation.
Integration With Directed Acyclic Graph (DAG) Consensus
Darklake’s infrastructure draws inspiration from DAG-based Byzantine Fault Tolerance (BFT) protocols like Fino, which decouple transaction dissemination from ordering to resist MEV attacks. In Fino, transactions are broadcast through a DAG structure, where causal relationships between messages ensure fairness without centralized sequencing. Darklake adapts this model by using a DAG to distribute encrypted transaction shares among validators, who collaboratively reconstruct the order only after cryptographic commitments are verified. This method eliminates single points of failure and reduces the risk of collusion among malicious validators.
Case Studies: MEV Exploitation On Solana & Darklake’s Role
The DeezNode Validator Incident
In March 2025, the Solana validator DeezNode demonstrated the devastating scalability of MEV attacks. By operating a private mempool and RPC cluster, DeezNode’s bots executed 1.55 million sandwich attacks in one month, extracting $13.43 million from unsuspecting traders. This incident highlighted the limitations of existing MEV solutions like Jito, which merely shifted exploitation to private networks rather than eliminating it. Darklake’s zkAMM could have mitigated this by rendering transaction data opaque to validators, removing their ability to prioritize malicious orders.
Wallet Draining & Phishing Vulnerabilities
A Reddit user reported losing all assets in their Solana wallet despite avoiding phishing links, with forensic analysis tracing the theft to a compromised trading bot linked to their Google account. Darklake’s MPC-based key management could prevent such breaches by distributing private key shards across nodes, ensuring no single entity holds complete access. Furthermore, its MEV Checker tool—which audits wallets for historical exploitation—provides users with transparency into potential vulnerabilities.
Comparative Analysis With Other MEV Mitigation Approaches
Threshold Encryption vs. ZKPs
Traditional MEV-resistant protocols like Fino rely on threshold encryption, where transactions are encrypted until a consensus threshold is reached. While effective, this approach introduces latency due to decryption overhead. Darklake’s use of ZKPs eliminates this delay by allowing validators to verify transactions without accessing their contents, achieving sub-second finality comparable to native Solana transactions.
AVID-M & Shared Secret Verification
Fino’s AVID-M protocol requires validators to exchange Merkle-tree-based shares of transaction keys, ensuring honesty through post-verification checks. Darklake simplifies this by integrating ZKPs directly into its DAG broadcast layer, reducing message complexity and computational overhead. Empirical data shows that Darklake’s approach achieves 99.9% MEV resistance with zero additional latency, outperforming AVID-M’s 95% resistance in simulated attacks.
Challenges & Future Directions For MEV-Resistant Protocols
Adoption Barriers & Network Effects
Despite its technical merits, Darklake faces adoption challenges due to Solana’s entrenched liquidity pools. Migrating liquidity from established DEXs like Raydium requires incentivizing liquidity providers (LPs) with higher yields or lower impermanent loss. Early data from Darklake’s incentivized testnet shows a 12% LP participation rate, suggesting the need for broader ecosystem partnerships.
Regulatory & Compliance Hurdles
Privacy-enhancing technologies often clash with financial surveillance mandates. Darklake’s encrypted transactions could attract regulatory scrutiny, particularly under frameworks like the EU’s Markets in Crypto-Assets (MiCA) regulation. To address this, the protocol incorporates optional travel rule compliance, allowing identified institutions to audit transactions without exposing user data.
How Darklake Redefines MEV Protection For Solana’s Decentralized Trading
Darklake represents a paradigm shift in MEV mitigation by combining zero-knowledge proofs, MPC, and DAG-based consensus to protect users from predatory trading practices. Its success hinges on overcoming liquidity fragmentation and regulatory challenges, but early results demonstrate unprecedented resistance to frontrunning and sandwich attacks. As blockchain networks scale, integrating privacy-preserving protocols like Darklake will be essential to maintaining user trust and ecosystem viability. Future research should explore hybrid models that balance transparency and privacy, ensuring DeFi’s evolution into a fair and inclusive financial infrastructure.






